Cloud-Native Web Security: Best Practices for Modern Deployments
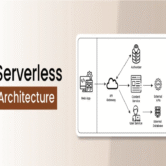
As web infrastructure increasingly moves to cloud environments, cloud-native web security has become essential for managing the unique complexities of modern deployments. Unlike monolithic systems, cloud-native applications are composed of distributed microservices, containers, and serverless functions that operate across dynamic environments. This architectural shift requires security strategies that are designed from the ground up for scalability, ephemerality, and automation. Static defenses are no longer sufficient; security must now be integrated directly into the orchestration, runtime, and deployment workflows.
A central best practice is adopting a policy-as-code approach, where security rules are defined in declarative formats and enforced programmatically during deployment. This ensures consistency, audibility, and repeatability across environments. Additionally, using runtime threat detection tools and container scanning pipelines helps identify vulnerabilities before and after deployment. Identity and access management at the service level is now mandatory, with fine-grained controls applied to APIs, data stores, and inter-service communication. These controls must be tied to immutable infrastructure principles, minimizing the risk of unauthorized modification.
Cloud-native security also emphasizes shift-left practices, where security is integrated early in the development lifecycle. This includes embedding security checks into CI/CD pipelines, enforcing secure defaults, and validating infrastructure configurations prior to production rollout. Encryption, both at rest and in transit, is enforced at all layers, and network segmentation isolates workloads for greater control. Overall, the focus is on building resilient, self-healing environments where security is intrinsic, rather than bolted on as an afterthought.