Explain How CSRF (Cross-Site Request Forgery) Exploits User Trust in Web Browsers
Introduction
Cross-Site Request Forgery (CSRF) is a deceptive web security threat that tricks users into performing unintended actions on a web application in which they are authenticated. Rather than exploiting system vulnerabilities or brute force, CSRF targets user trust—specifically the trust a web browser places in a user’s authenticated session. This makes it one of the more subtle and dangerous forms of web exploitation, particularly when user sessions involve sensitive operations like fund transfers, profile changes, or data submissions.
Understanding Browser Trust in Sessions
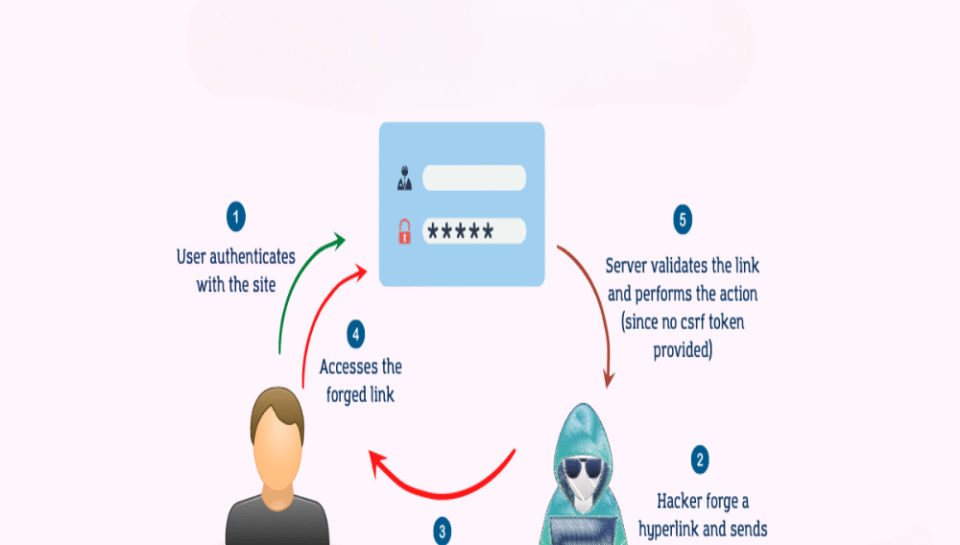
When users log into a web application, such as a bank or email account, their browser stores a session token or authentication cookie. This token allows the user to remain logged in and perform actions without re-entering credentials for every request. Web applications trust the browser to send this token with each request, assuming the actions are initiated by the user.
How CSRF Exploits This Trust
CSRF takes advantage of this automatic behavior. If an attacker tricks a user into visiting a malicious website while logged into a legitimate one, the malicious site can trigger a request to the legitimate site using the user’s browser. Because the browser includes the valid session token or cookie with the request, the server assumes the request is legitimate and processes it as if the user had initiated it.
Manipulating Unintended Actions
The attack works without the user’s awareness and often without any visible interaction. The attacker cannot see the user’s data, but they can manipulate actions—like changing account details, making purchases, or posting content—by exploiting the trusted session. This form of deception turns the user’s own browser into a weapon against them.
No Need to Breach the Server
One of the most dangerous aspects of CSRF is that the attacker does not need to breach the website’s server or bypass any authentication barriers. Instead, the attacker counts on the browser’s cooperation in including the stored credentials. It’s a social-engineering-based approach that relies on user behavior and web application design flaws rather than technical vulnerabilities.
Web Applications Vulnerable to CSRF
Applications that do not verify the origin of requests are especially vulnerable. If a web application relies solely on cookies for authentication and does not use additional verification methods (like tokens or referer checks), it becomes an easy target for CSRF attacks.
Consequences of a Successful CSRF Attack
CSRF can result in serious damage: unauthorized fund transfers, stolen loyalty points, changed passwords or email addresses, or even data deletion. The attack impersonates the user’s intent and can severely undermine trust in digital services—especially in financial, healthcare, and government platforms.
Preventive Measures
To counter CSRF, modern web applications implement anti-CSRF tokens, which are unique to each session and embedded in forms or request headers. These tokens must match server-side values for the request to be accepted. Other protections include SameSite cookie attributes, double-submit cookies, referer validation, and user re-authentication for critical actions.
Conclusion
CSRF is a silent but potent attack that exploits the inherent trust web browsers place in authenticated users. By manipulating session behavior, it enables attackers to act on behalf of unsuspecting users. In the current digital ecosystem, protecting against CSRF is a fundamental component of responsible web application development and management.
Hashtags
#CSRF #CrossSiteRequestForgery #WebSecurity #CyberSecurity #BrowserTrust #SessionSecurity #WebApplicationSecurity #SecureWebDevelopment #CyberAwareness #TokenAuthentication #AntiCSRF #WebThreats #UserTrustExploitation #DigitalSecurity #CyberHygiene #AuthenticationRisks #SecureWebSessions #OnlineProtection #WebExploitPrevention #SecurityTokens #SecureCoding #CyberThreatsIndia #DigitalTrust #WebVulnerability #WebAttackPrevention





