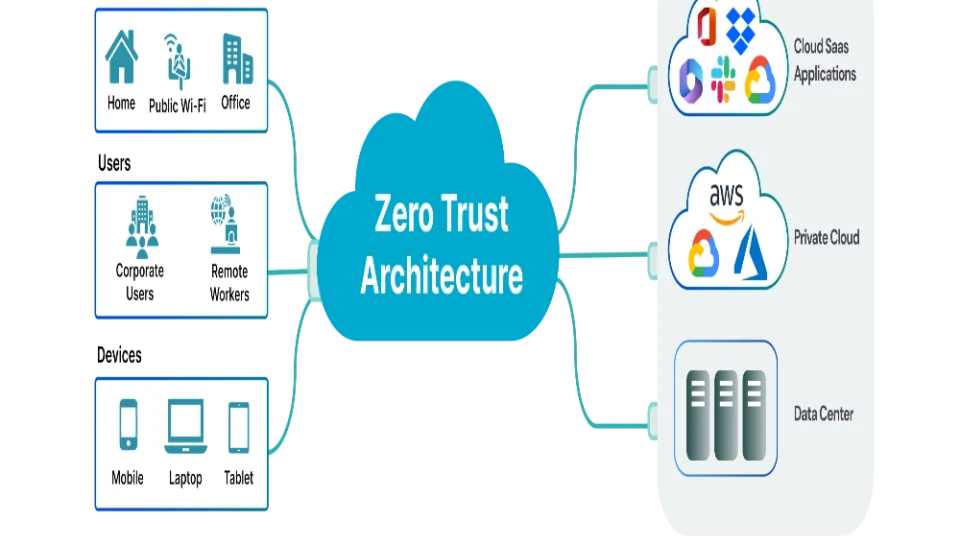
Explain the Concept of Zero Trust Architecture in Web Security Contexts
Introduction
In today’s cyber landscape, where data breaches, insider threats, and sophisticated attacks have become the norm, traditional perimeter-based security models are proving increasingly ineffective. These outdated models operate on the assumption that anything inside the network can be trusted. However, with the rise of cloud computing, remote work, mobile access, and third-party integrations, this trust model leaves too many blind spots. Enter Zero Trust Architecture (ZTA)—a modern security framework designed to overcome these challenges by eliminating implicit trust and enforcing continuous verification of every user and device. In web security contexts, Zero Trust provides a robust, flexible approach to safeguarding web applications, APIs, and data across dynamic and distributed environments.
Zero Trust Architecture
Zero Trust Architecture is a security model that operates on the principle of “never trust, always verify.” It assumes that threats can originate both outside and inside the network, and thus, no user or system—regardless of location—should be trusted by default. Instead of a single, secure perimeter, Zero Trust continuously validates trust at every access point using authentication, authorization, and context-based policies. This approach focuses on minimizing attack surfaces and controlling access at a granular level, making it especially relevant in web environments where users and services are highly distributed.
Core Principles of Zero Trust
- Verify Explicitly: Always authenticate and authorize based on all available data points, such as user identity, device health, location, and behavior.
- Use Least Privilege Access: Limit user access rights to only what is necessary to perform their tasks, reducing potential lateral movement.
- Assume Breach: Design systems under the assumption that a breach has occurred or will occur. Apply strict segmentation and monitoring accordingly.
These principles form the foundation for a secure and adaptive environment, where no user or system is inherently trusted without validation.
Application of Zero Trust in Web Security
Web applications, being internet-facing, are prime targets for exploitation. Zero Trust helps secure them by ensuring that access to web resources is tightly controlled and contextually evaluated. In practice, this includes enforcing Multi-Factor Authentication (MFA), identity-aware proxies, session validation, and API access controls. Unlike traditional models where authentication is a one-time event, Zero Trust treats every access request as suspicious, continuously verifying credentials and context before granting or maintaining access.
Authentication and Identity Management
Strong identity verification is at the heart of Zero Trust. Web systems under Zero Trust enforce robust identity and access management (IAM) mechanisms, including:
- Single Sign-On (SSO) to streamline secure logins
- Multi-Factor Authentication (MFA) to verify identity beyond passwords
- Behavioral biometrics and risk-based authentication to adapt to anomalies
This ensures that access is granted only to legitimate users and devices under secure conditions, even if they’re within the organizational network.
Micro-Segmentation and Access Control
Zero Trust environments utilize micro-segmentation, which divides the network and application environment into small zones. Each segment has its own access controls and policies. For web platforms, this means isolating different components such as user authentication, backend APIs, databases, and admin panels. Unauthorized access to one area does not grant access to others, thereby containing threats and reducing the potential impact of a breach.
Device and Endpoint Security
In web contexts, users often access platforms from various devices, including laptops, smartphones, and tablets. Zero Trust requires continuous evaluation of device health—checking for up-to-date software, secure configurations, and compliance with company policies. Only secure, verified devices are granted access to web resources. Endpoint Detection and Response (EDR) tools, along with Mobile Device Management (MDM), play a crucial role in enforcing these policies.
Data Protection and Encryption
Zero Trust mandates that sensitive data be encrypted both in transit and at rest. Web applications must implement HTTPS with TLS, secure cookies, data masking, and storage encryption protocols. By controlling who accesses what data and under which conditions, Zero Trust prevents data exfiltration and unauthorized manipulation, even in the event of compromised credentials or devices.
Logging, Monitoring, and Incident Response
Zero Trust frameworks emphasize continuous monitoring and real-time threat detection. Security teams must log every access attempt, analyze behavioral patterns, and flag anomalies for investigation. Integration with Security Information and Event Management (SIEM) systems and automated incident response platforms ensures quick detection and remediation of threats. In web applications, this includes monitoring traffic patterns, login behaviors, and API interactions.
Zero Trust for API Security
Modern web applications are often powered by APIs, which are increasingly targeted by attackers. Under Zero Trust, each API request must be authenticated and validated for legitimacy. This includes using OAuth tokens, API gateways, and rate-limiting strategies to prevent abuse. Treating each API interaction as untrusted unless proven secure ensures the integrity and confidentiality of data exchanges between services.
Implementing Zero Trust in Web Development
To integrate Zero Trust in the web development lifecycle, developers and security teams must adopt secure coding practices, conduct regular code reviews, and implement secure deployment pipelines. Continuous integration/continuous deployment (CI/CD) tools should be integrated with security scanners to detect vulnerabilities before code reaches production. DevSecOps—embedding security throughout the development process—is key to ensuring that web applications are Zero Trust-ready from day one.
Benefits of Zero Trust for Web Security
- Reduced Attack Surface: Limits exposure by controlling access at every layer.
- Improved Incident Containment: Segmentation and least privilege policies isolate threats.
- Enhanced Visibility: Continuous monitoring provides real-time insight into all user and device activity.
- Stronger Compliance Posture: Aligns with regulations like GDPR, HIPAA, and NIST.
- Future-Proof Security: Adaptable to hybrid environments, remote work, and cloud-native applications.
Conclusion
Zero Trust Architecture represents a paradigm shift in cybersecurity, replacing outdated trust-based models with a dynamic, identity-centric approach. In web security contexts, Zero Trust ensures that every user, request, and device is rigorously verified, regardless of its origin. By enforcing strict access controls, continuous monitoring, and encryption, Zero Trust minimizes vulnerabilities and enhances the overall resilience of web platforms. As threats grow in complexity and frequency, adopting a Zero Trust model is not only a best practice—it is a critical necessity for safeguarding digital assets in the modern web era.
Hashtags
#ZeroTrust #WebSecurity #CyberSecurity #AccessControl #ZeroTrustArchitecture #ZTNA #DataProtection #APIsecurity #WebAppSecurity #LeastPrivilege #IdentityManagement #MicroSegmentation #MFA #SecureWebApps #SecurityByDesign #NetworkSecurity #CloudSecurity #Authentication #DevSecOps #SIEM #HTTPS #DataEncryption #TrustNoOne #SecureDevelopment #WebPlatformSecurity





